The Enemy Within IoT - A Mirai DDoS Timeline
•
4 gostaram•3,023 visualizações
A new devastating tool by the name of Mirai was used in the attack on Dyn - the largest DDoS in history. It achieved this by using Internet of Things (IoT) devices as a botnet to great effect. How did we get here?
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...![[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...Stowarzyszenie Jakości Systemów Informatycznych (SJSI)
Recomendados
[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...![[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...Stowarzyszenie Jakości Systemów Informatycznych (SJSI)
Mais conteúdo relacionado
Mais procurados
Mais procurados (16)
Cisco Visual Networking Index Graphic--By the Numbers

Cisco Visual Networking Index Graphic--By the Numbers
FIWARE MEXICO WorkShop 2016 - 7. Example of FIWARE Applications by INFOTEC

FIWARE MEXICO WorkShop 2016 - 7. Example of FIWARE Applications by INFOTEC
Introducción a Briar: inter-conectarse sin internet

Introducción a Briar: inter-conectarse sin internet
The Impact of IoT on Enterprise Wi-Fi by AirTight Networks via Slideshare

The Impact of IoT on Enterprise Wi-Fi by AirTight Networks via Slideshare
John harrobin verizon wireless and skype to have news conference at ctia

John harrobin verizon wireless and skype to have news conference at ctia
CE Cybersecurity Trends and Strategies for Hosting in the Cloud

CE Cybersecurity Trends and Strategies for Hosting in the Cloud
Semelhante a The Enemy Within IoT - A Mirai DDoS Timeline
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updatesBriskinfosec Technology and Consulting
Semelhante a The Enemy Within IoT - A Mirai DDoS Timeline (20)
Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...

Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates
Case Study: Wannacry Ransomware attacks Telefónica

Case Study: Wannacry Ransomware attacks Telefónica
Mais de InterQuest Group
Mais de InterQuest Group (20)
Último
Último (9)
IP addressing and IPv6, presented by Paul Wilson at IETF 119

IP addressing and IPv6, presented by Paul Wilson at IETF 119
Company Snapshot Theme for Business by Slidesgo.pptx

Company Snapshot Theme for Business by Slidesgo.pptx
Cybersecurity Threats and Cybersecurity Best Practices

Cybersecurity Threats and Cybersecurity Best Practices
SCM Symposium PPT Format Customer loyalty is predi

SCM Symposium PPT Format Customer loyalty is predi
The Enemy Within IoT - A Mirai DDoS Timeline
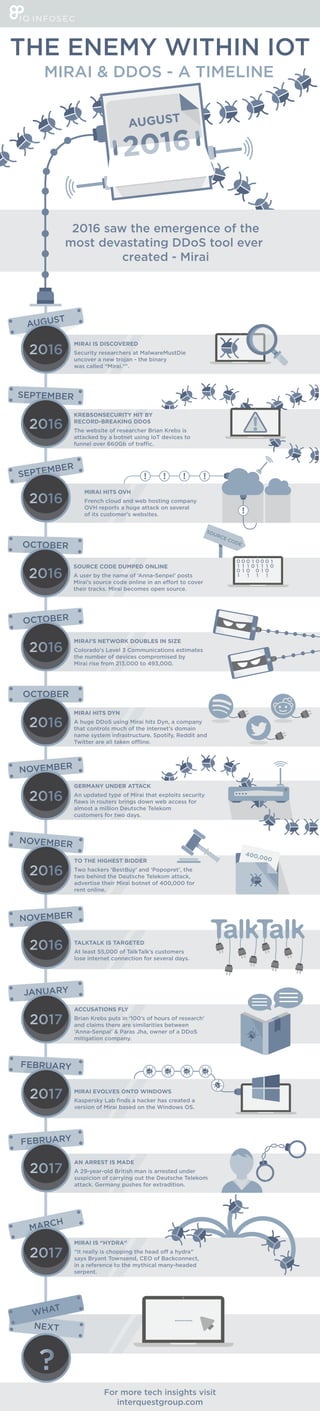
- 1. SEPTEMBER KREBSONSECURITY HIT BY RECORD-BREAKING DDOS The website of researcher Brian Krebs is attacked by a botnet using IoT devices to AUGUST MIRAI IS DISCOVERED Security researchers at MalwareMustDie uncover a new trojan - the binary was called “Mirai.*”. SEPTEMBER OCTOBER SOURCE CODE DUMPED ONLINE A user by the name of ‘Anna-Senpei’ posts their tracks. Mirai becomes open source. OCTOBER MIRAI’S NETWORK DOUBLES IN SIZE Colorado's Level 3 Communications estimates the number of devices compromised by Mirai rise from 213,000 to 493,000. SOURCE CODE OCTOBER MIRAI HITS DYN A huge DDoS using Mirai hits Dyn, a company that controls much of the internet’s domain name system infrastructure. Spotify, Reddit and MIRAI HITS OVH French cloud and web hosting company OVH reports a huge attack on several of its customer's websites. NOVEMBER GERMANY UNDER ATTACK An updated type of Mirai that exploits security flaws in routers brings down web access for almost a million Deutsche Telekom customers for two days. NOVEMBER TO THE HIGHEST BIDDER Two hackers ‘BestBuy’ and ‘Popopret’, the two behind the Deutsche Telekom attack, advertise their Mirai botnet of 400,000 for rent online. NOVEMBER TALKTALK IS TARGETED At least 55,000 of TalkTalk’s customers lose internet connection for several days. JANUARY ACCUSATIONS FLY Brian Krebs puts in ‘100’s of hours of research’ and claims there are similarities between ‘Anna-Senpai’ & Paras Jha, owner of a DDoS mitigation company. FEBRUARY MIRAI EVOLVES ONTO WINDOWS Kaspersky Lab finds a hacker has created a version of Mirai based on the Windows OS. FEBRUARY AN ARREST IS MADE A 29-year-old British man is arrested under suspicion of carrying out the Deutsche Telekom attack. Germany pushes for extradition. MARCH MIRAI IS “HYDRA” says Bryant Townsend, CEO of Backconnect, in a reference to the mythical many-headed serpent. THE ENEMY WITHIN IOT MIRAI & DDOS - A TIMELINE 2016 saw the emergence of the most devastating DDoS tool ever created - Mirai NEXT WHAT For more tech insights visit interquestgroup.com ...........
